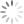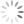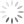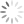Azure - Application Security group
Azure — Application Security group
Application security groups enable you to configure network security as a natural extension of an application’s structure, allowing you to group virtual machines and define network security policies based on those groups. You can reuse your security policy at scale without manual maintenance of explicit IP addresses. The platform handles the complexity of explicit IP addresses and multiple rule sets, allowing you to focus on your business logic.
Application Security Groups helps to manage the security of Virtual Machines by grouping them according to the applications that run on them. It is a feature that allows the application-centric use of Network Security Groups.
This approach allows for the grouping of Virtual Machines logically, irrespective of their IP address or subnet assignment within a Virtual Network.
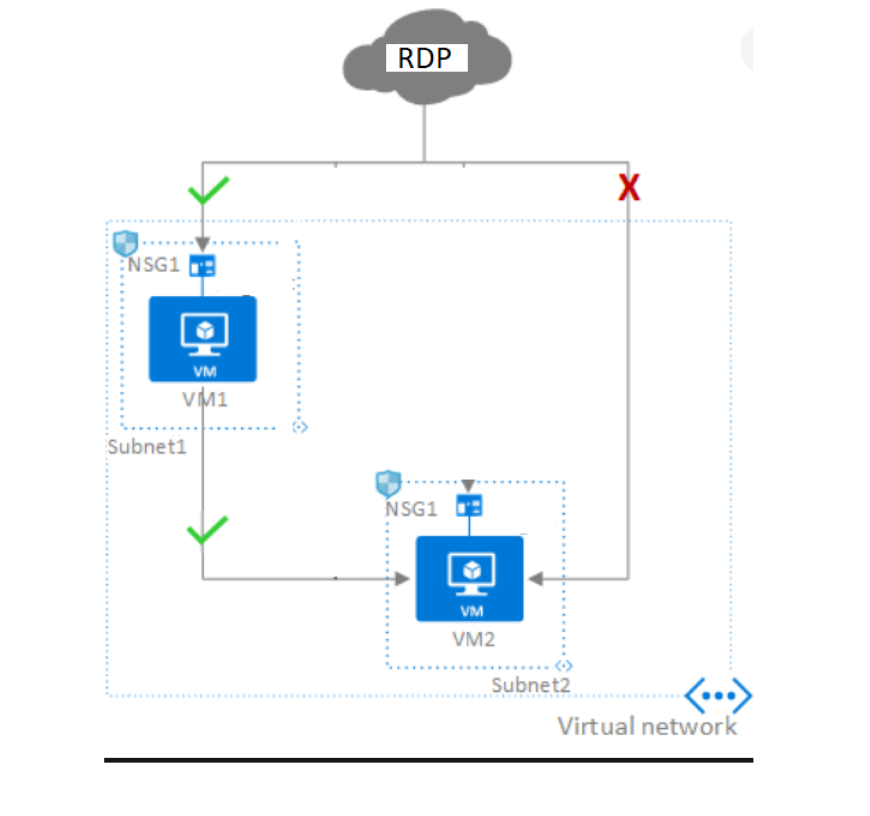
whenever you deploy a network security group (NSG) it is either assigned to a NIC or a subnet. If you deploy that NSG to a subnet then the rules apply to all of the NICs, or virtual machines, in that subnet.
ASGs are used within an NSG to apply a network security rule to a specific workload or group of VMs — defined by ASG worked as being the “network object” & explicit IP addresses are added to this object. This provides the capability to group VMs into associated groups or workloads, simplifying the NSG rule definition process. Another great use of this is for scalability, creating the virtual machine and assigning the newly created virtual machine to its ASG will provide it with all the NSG rules in place for that specific ASG.
Benefits:
- It reduces the need for creating or updating NSG every time you add a server to the existing application set.
- Allow point to point communication with less number of NSG rules.
As a part of this demo, I will be showing a few different ways to implement the usage of Application Security Groups.
- using a single Virtual network with multiple subnets
- using multiple Virtual networks with a single subnet.
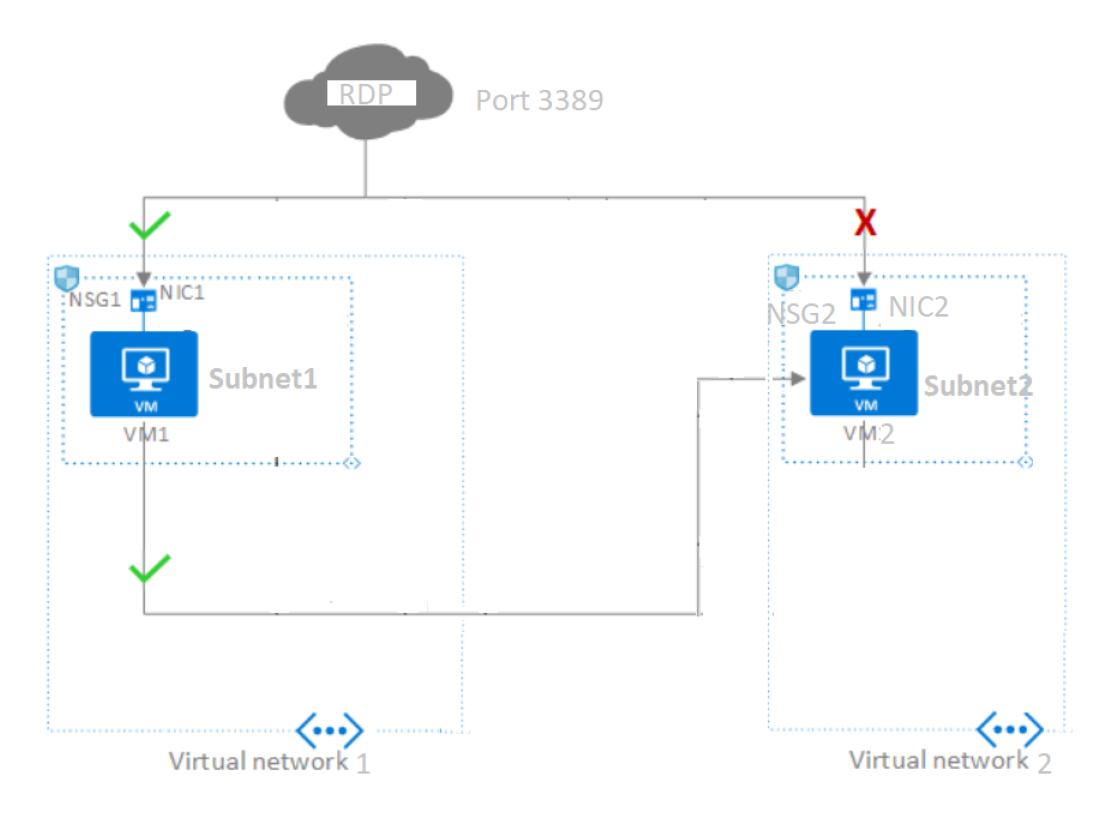
- As a part of the first scenario with using a single Virtual network with 2 subnets, 2 Application Security groups to route traffic flow using a single virtual network between 2 Azure VM’s.
As a pre-requisite we need
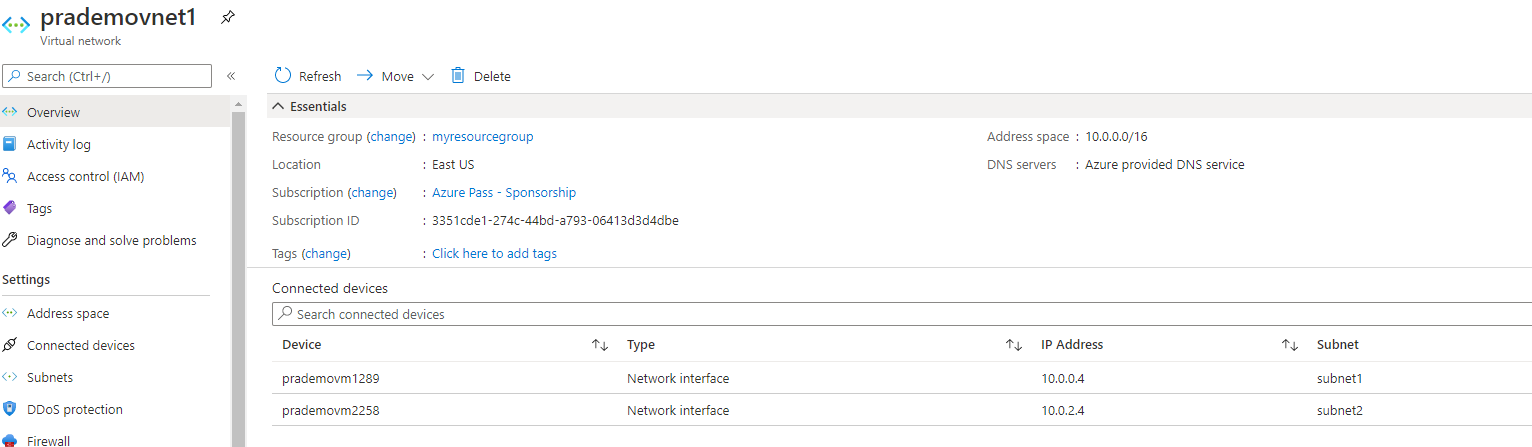
a. Create 1 virtual network with an Address space of 10.0.0.0/16
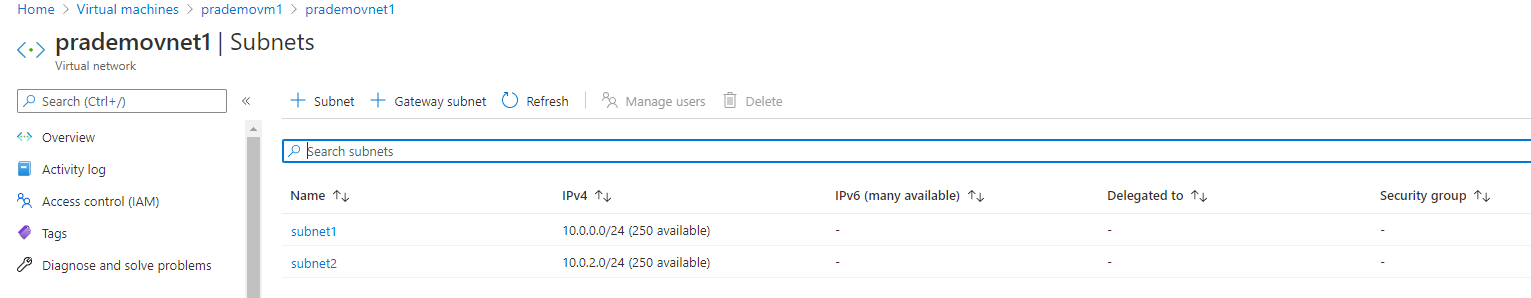
b. Create 2 subnets:
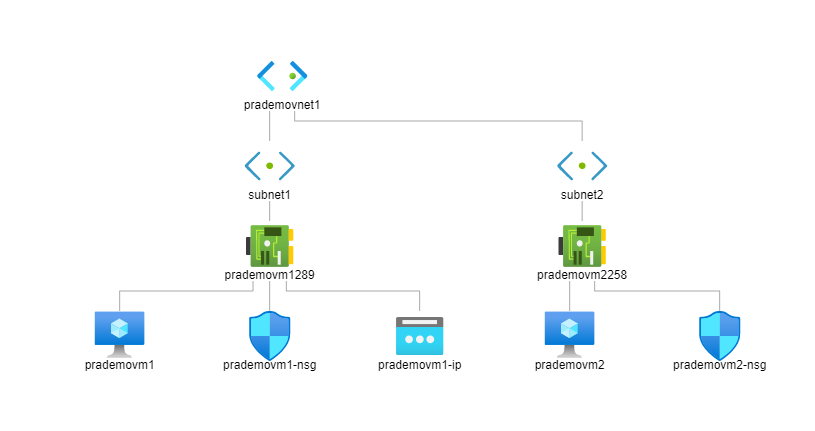
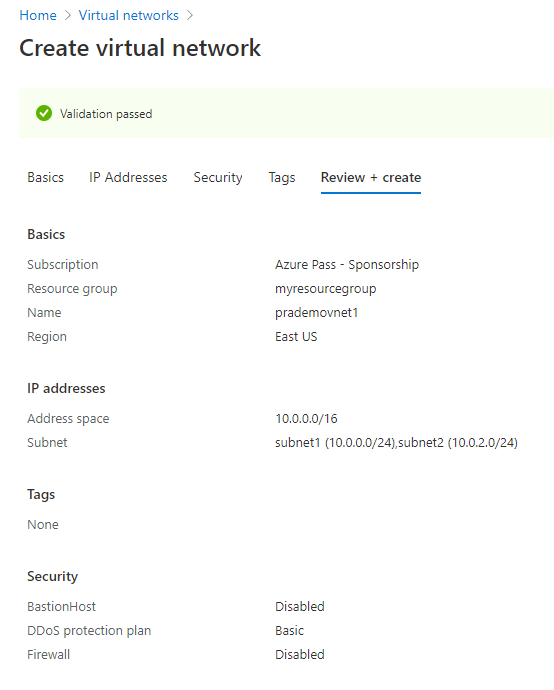
- Subnet1: 10.0.0.0/24
- Subnet2: 10.0.2.0/24
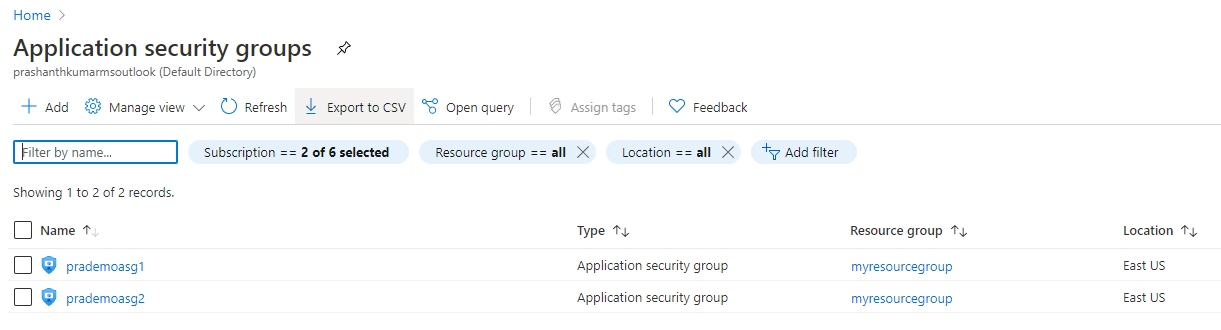
c. create 2 new ASG’s
d. Now lets create 2 Azure Virtual Machines
Associate first Azure VM with current virtual network1 with Subnet1
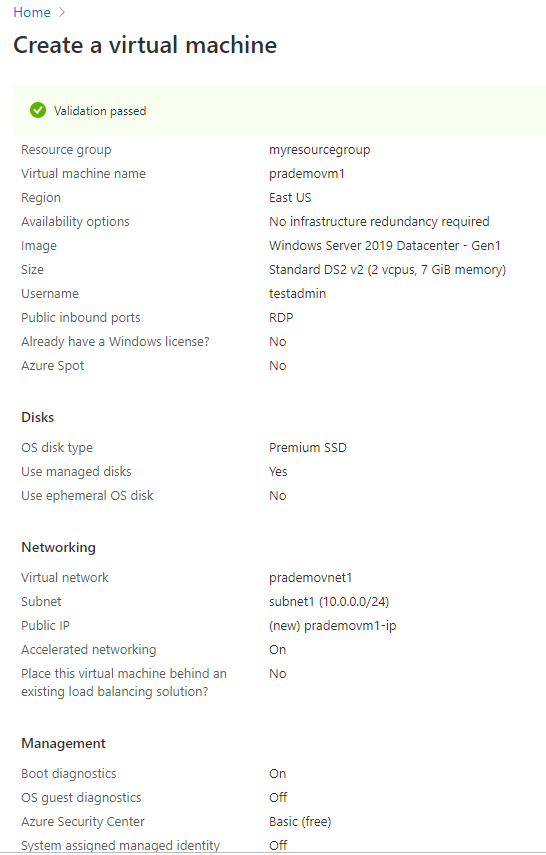
4b. Now let's create our second VM with 2nd Vnet + subnet2 but with no public IP address.
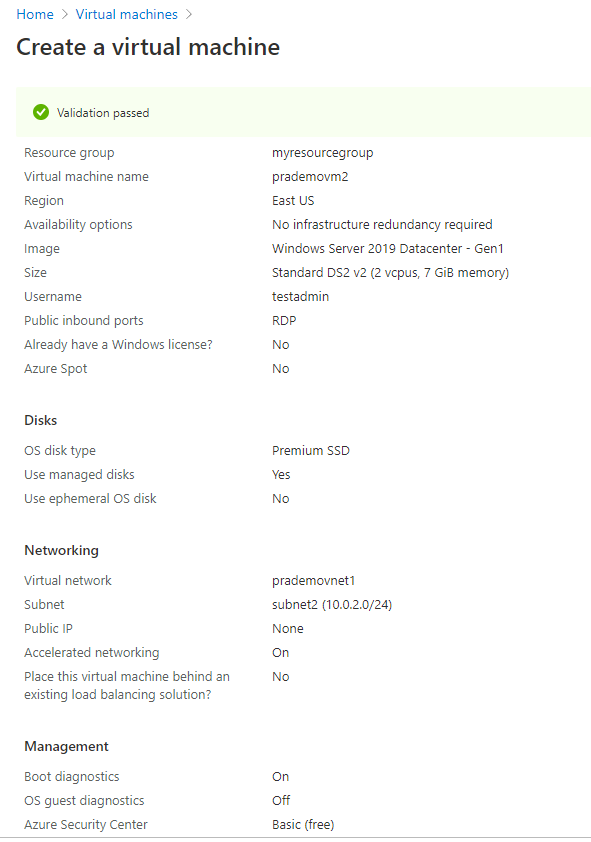
Now, let's start associating ASG rules to the virtual networks to test traffic.
- Go to Azure Portal → go to the first VM properties page → click on Networking → click on “Application Security groups”
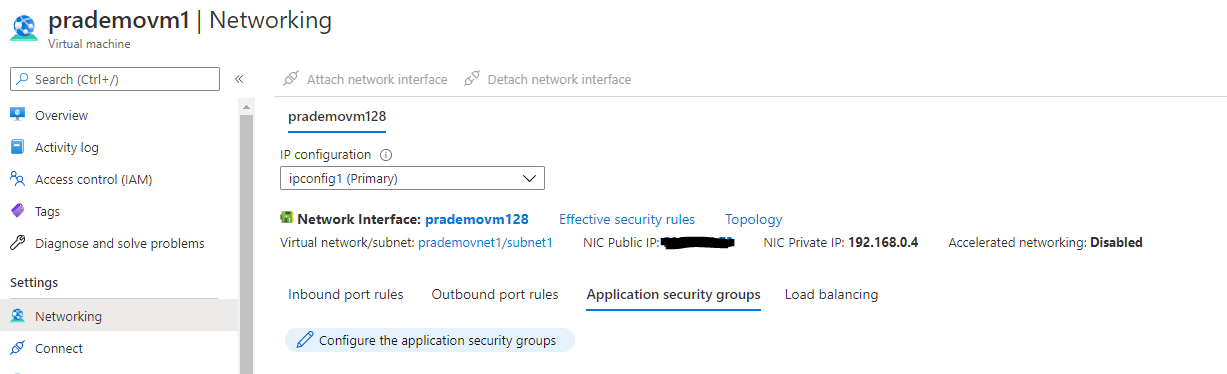
2. It will open a new page and now select appropriate ASG to attach it with 1st VM. → click Save
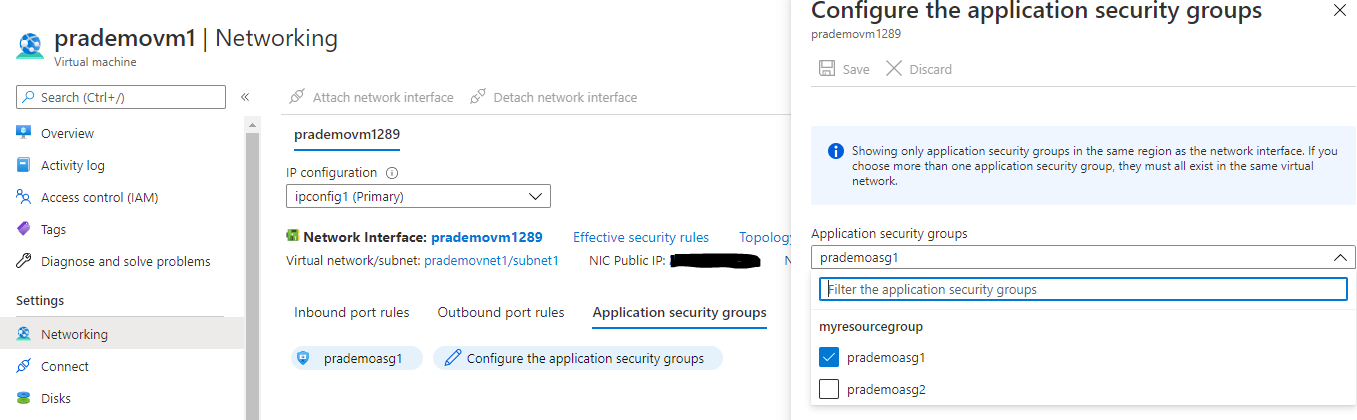
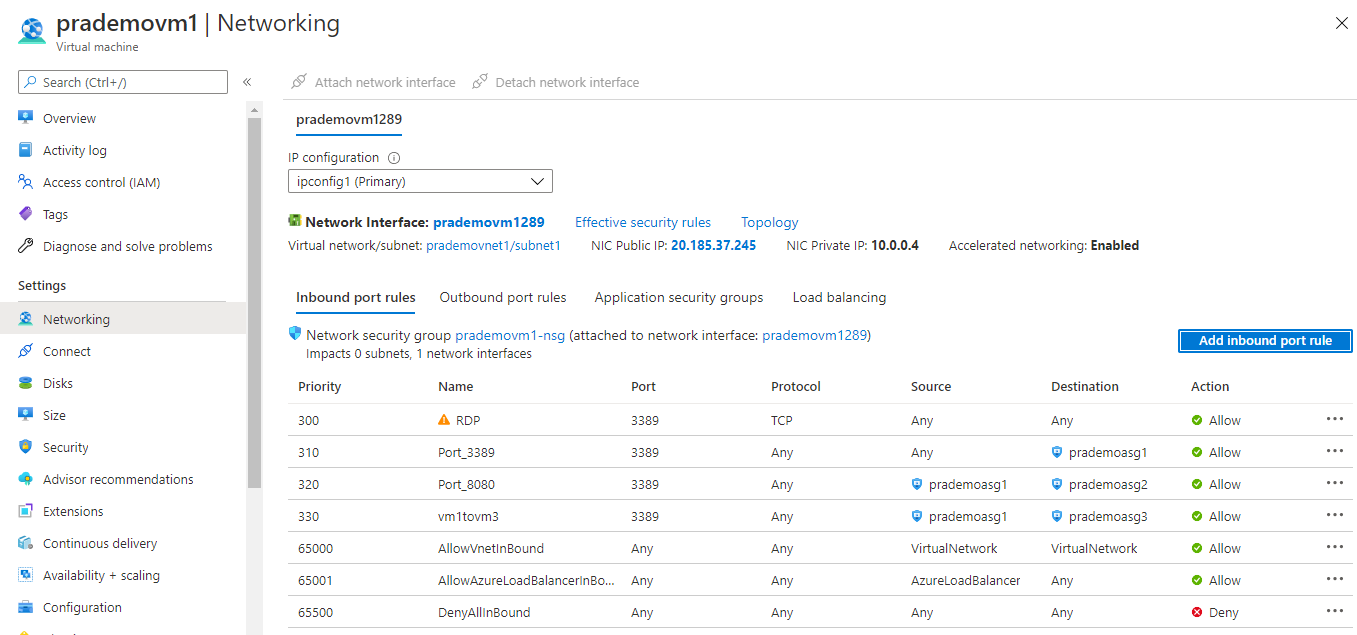
3. Now as a part of testing we want to route the RDP port to VM2, for that → click on Inbound port rules → select Destination as prademoasg1 → click Add.
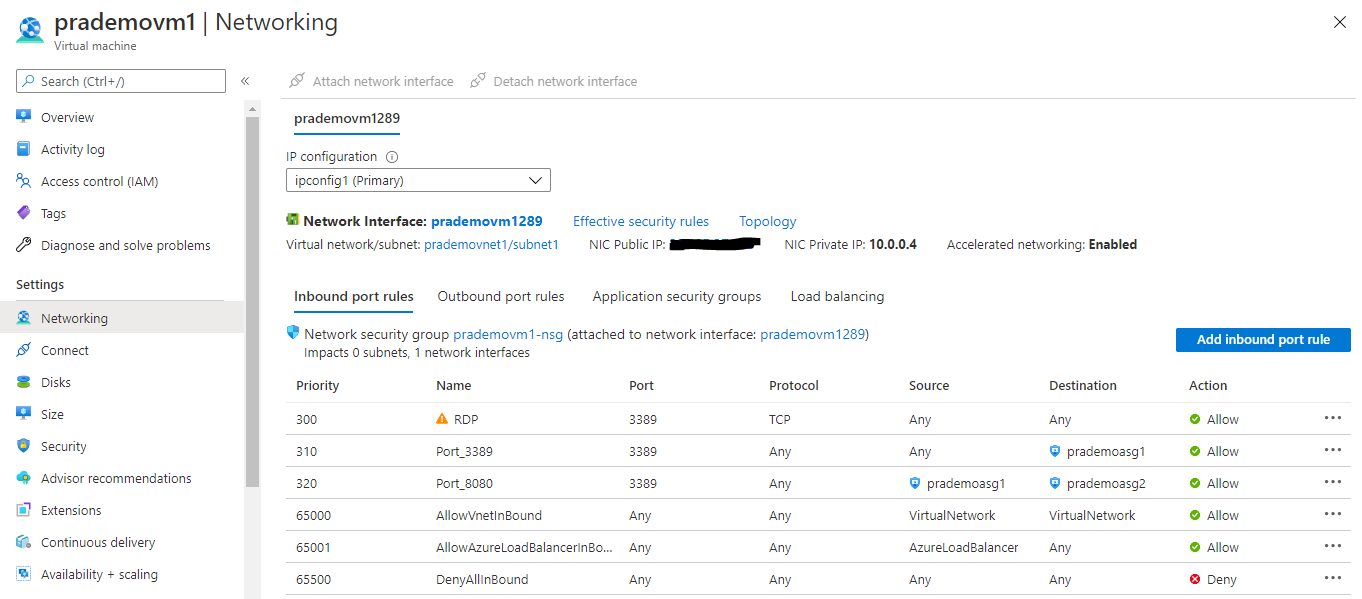
Now let's configure traffic rules for VM2
Here you can see we don’t have any RDP rule mentioned yet under Inbound port rules.
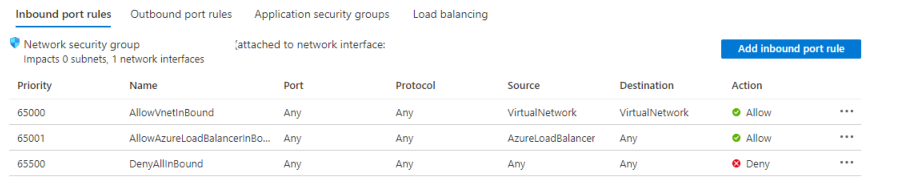
Now once again click on Inbound port rules → create a new rule → select below options → Add
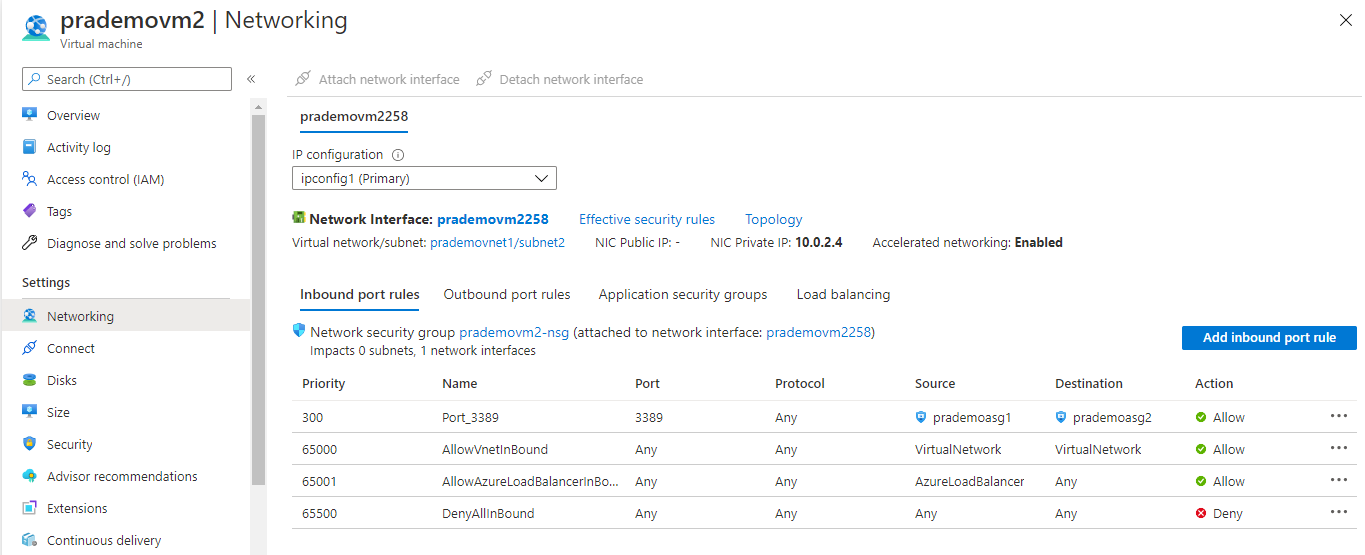
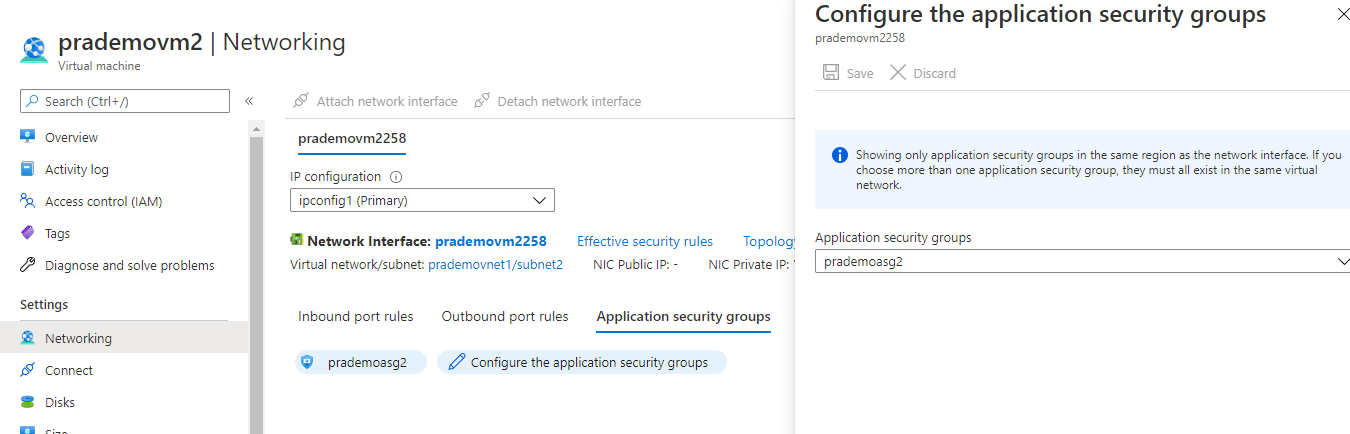
Let's add the Application Security group to route the traffic from VM1 to VM2.
for this click on Application Security group → click on “configure Application Security groups” → select Prademoasg2 → Save
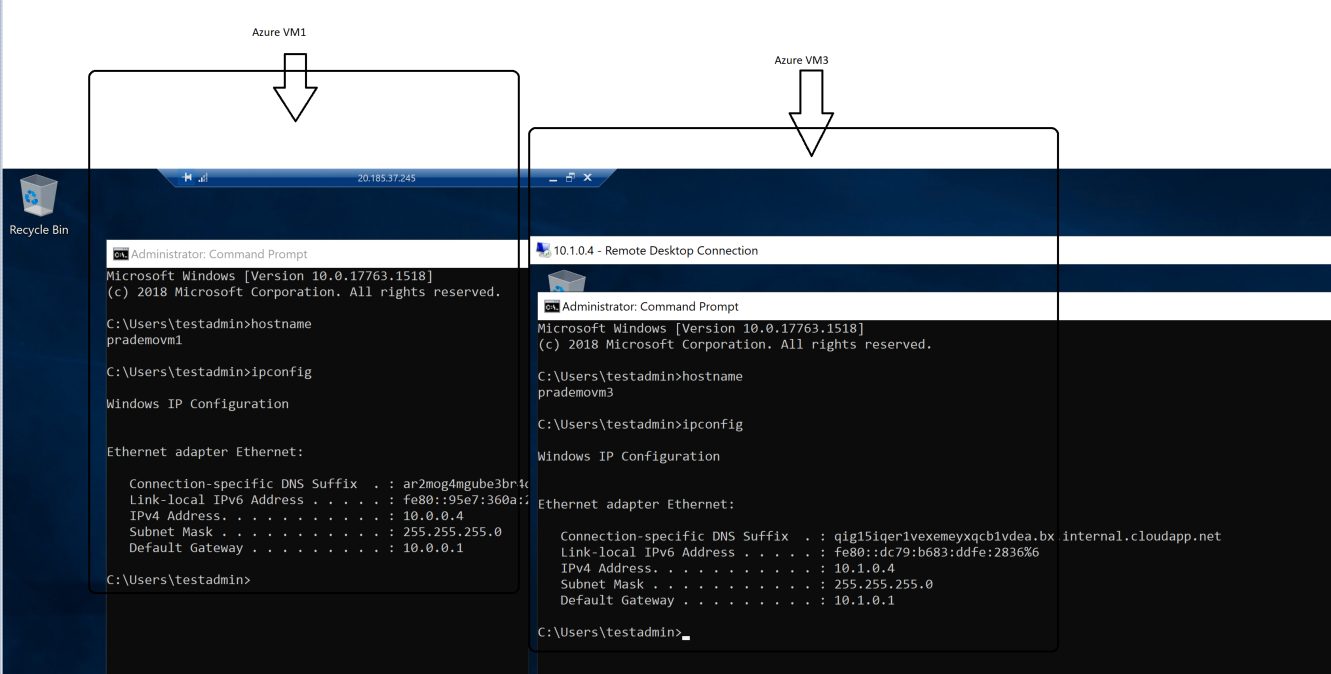
Now let's do the final RDP validation → Try connecting to Azure VM1
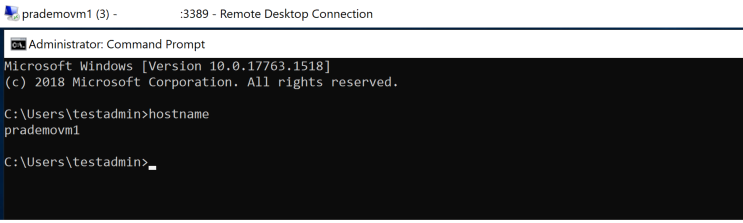
Once you connect to Azure VM1 → validate the hostname
Now let's open a new RDP session to Azure VM2 which doesn't have any Public IP at this moment, it just has a private IP address.
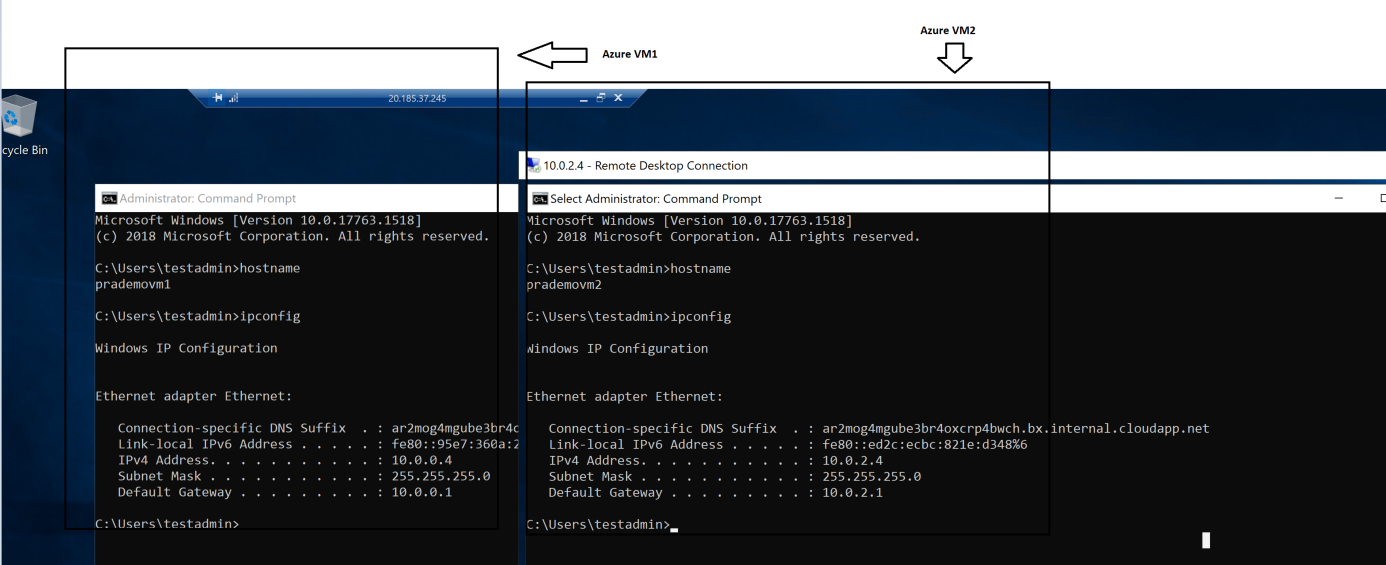
Azure VM1 shows Public & Private IP address
Azure VM2 we connected via Private IP address
Scenario 2: using Multi Virtual networks with a single subnet.
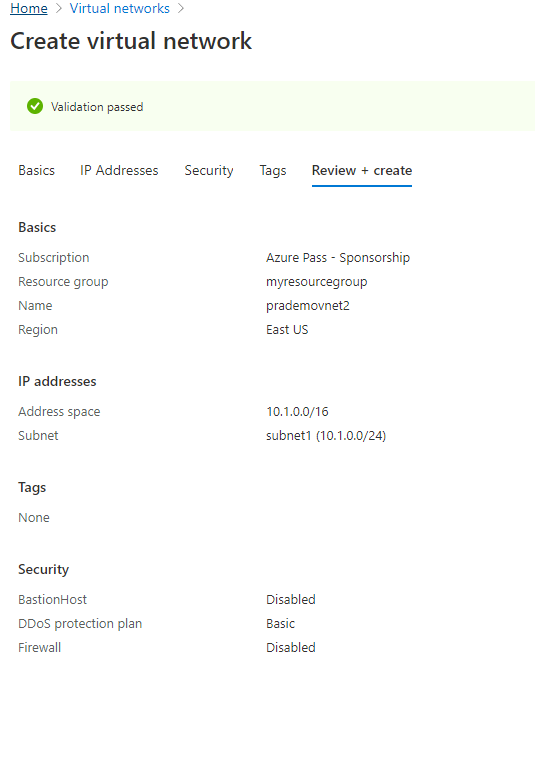
- Let's create a new Virtual network with the name: Prademovnet2
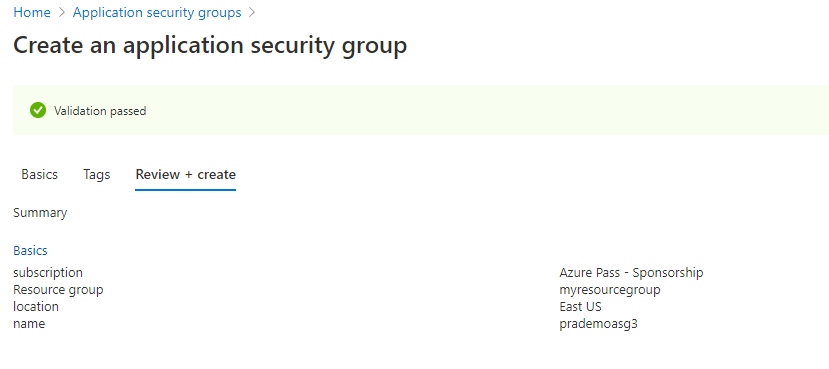
2. Create a new Application Security group
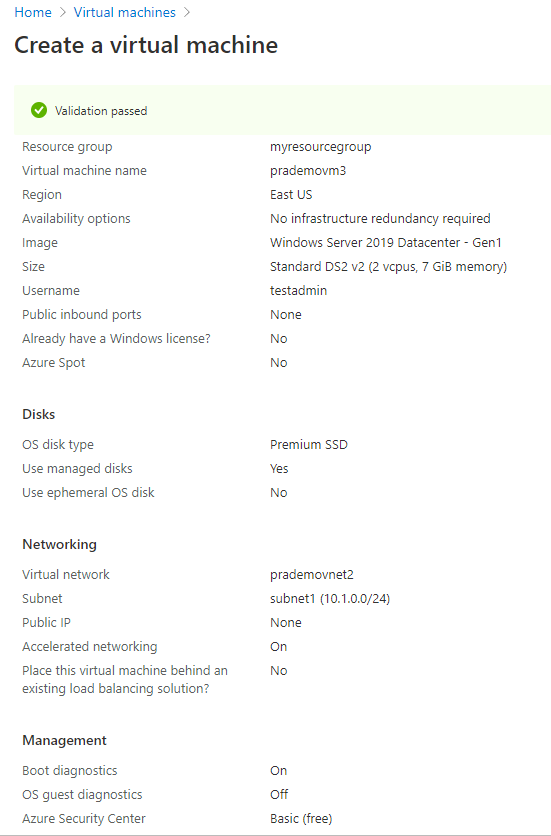
3. Let's create our 3rd Azure VM and Associate this newly created virtual network (prademovnet2) with this, and with no Public IP address
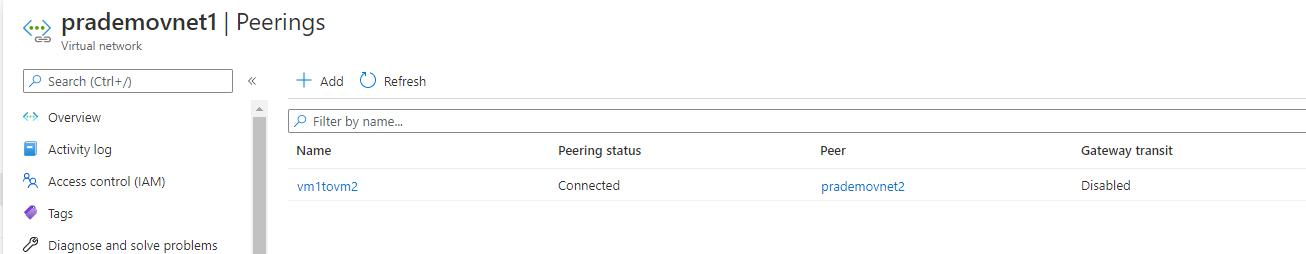
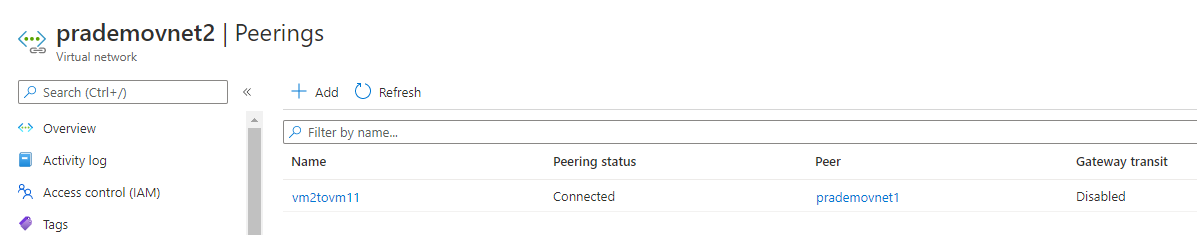
4. As we are using 2 virtual networks so we need to peer them first. So go to Azure Portal → go to virtual networks → click on the first virtual network → under Settings → click on Peering's → click on + →
5. Now in order to test actual routing → goes to Azure VM1 → go to networking → click on Add inbound port rule →
Source: Application Security group
Source application security group: prademoasg1
Source port ranges : *
Destination: Application Security group
Destination Application Security group: prademoasg3
Destination port ranges: 3389
protocol: Any
Action: Allow
Priority: 330
Name : vm1tovm3
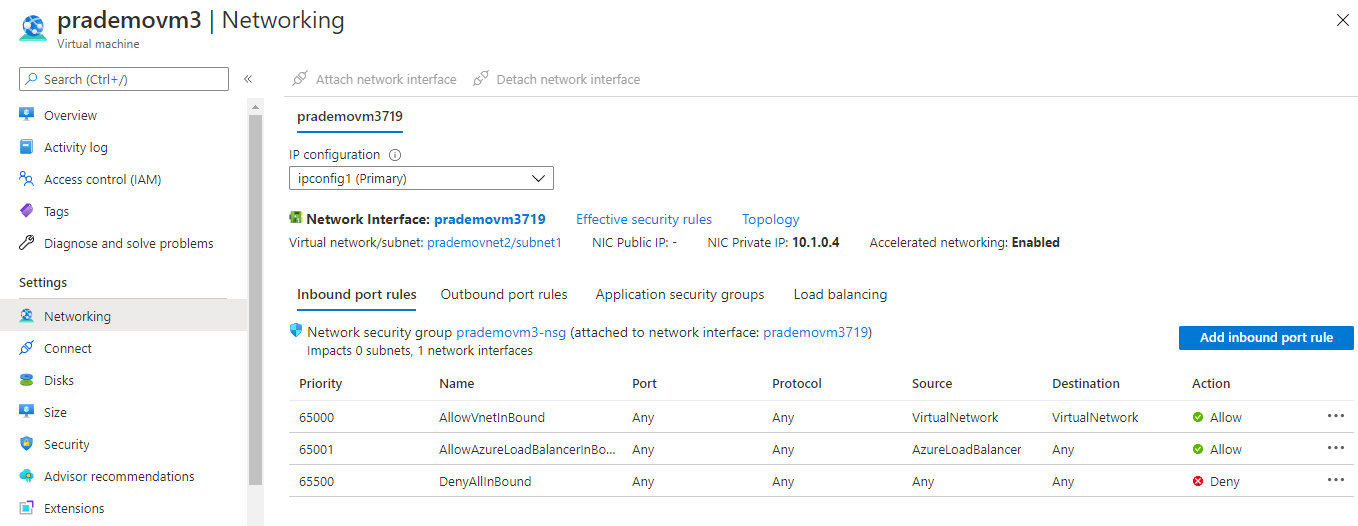
6. Now let's go to Azure VM3 → go to networking and Add Application Security group so that this VM can start taking RDP traffic.
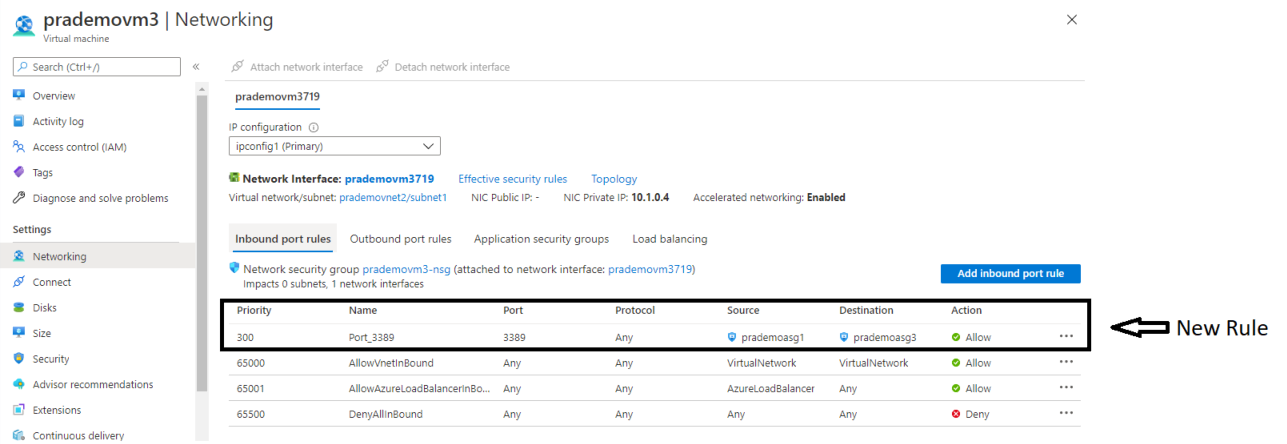
Now let's add a new Application Security group
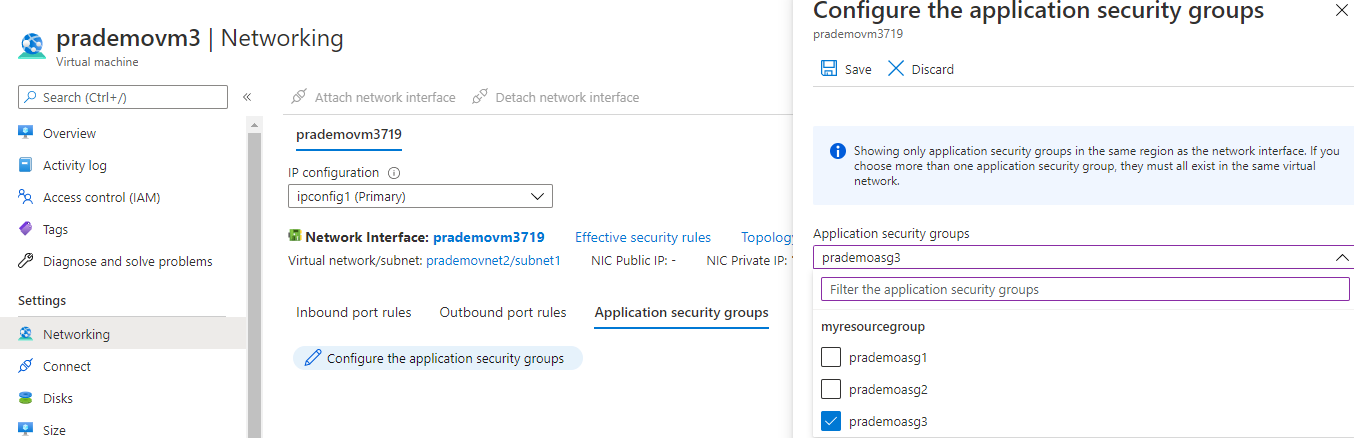
Finally, let's test the RDP connection from Azure VM1 to Azure VM3